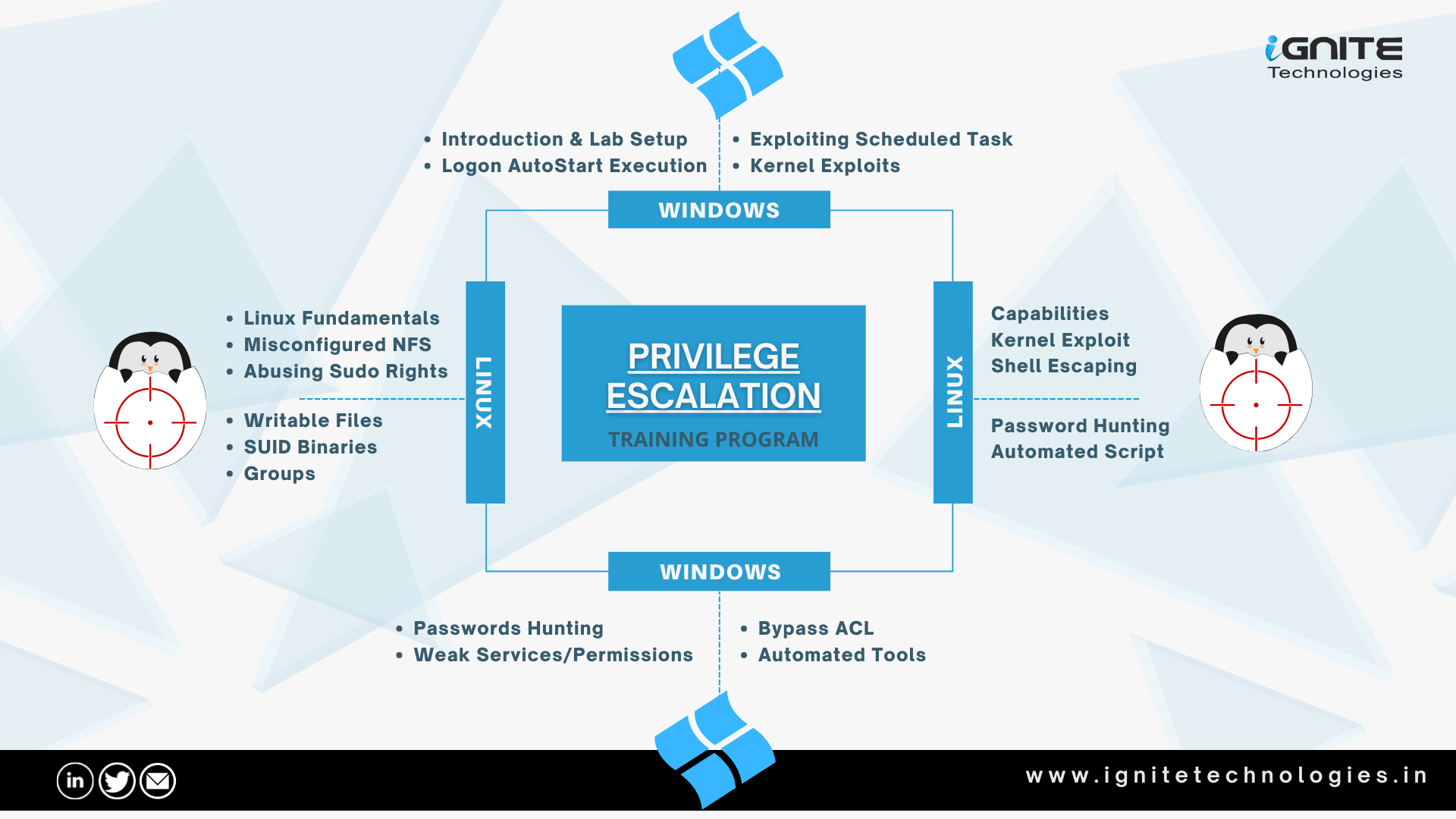
dragon21 on X: "RT @hackinarticles: Privilege Escalation Tools https://t.co/XqqsyaoRch #infosec #cybersecurity #cybersecuritytips #pentesting #oscp #redt…" / X

Linux Exploit Suggester - Linux Privilege Escalation Auditing Tool - Kali Linux 2018.1 – PentestTools
![Linux Privilege Escalation - Automated Tools [HINDI] | Part_02 | PentestHint | LinPeas Tutorial - YouTube Linux Privilege Escalation - Automated Tools [HINDI] | Part_02 | PentestHint | LinPeas Tutorial - YouTube](https://i.ytimg.com/vi/p-MoSi5WvIM/maxresdefault.jpg)
Linux Privilege Escalation - Automated Tools [HINDI] | Part_02 | PentestHint | LinPeas Tutorial - YouTube
![Linux Privilege Escalation - Automated Tools [HINDI] | Part_02 | PentestHint | LinPeas Tutorial - YouTube Linux Privilege Escalation - Automated Tools [HINDI] | Part_02 | PentestHint | LinPeas Tutorial - YouTube](https://i.ytimg.com/vi/p-MoSi5WvIM/hqdefault.jpg)
Linux Privilege Escalation - Automated Tools [HINDI] | Part_02 | PentestHint | LinPeas Tutorial - YouTube

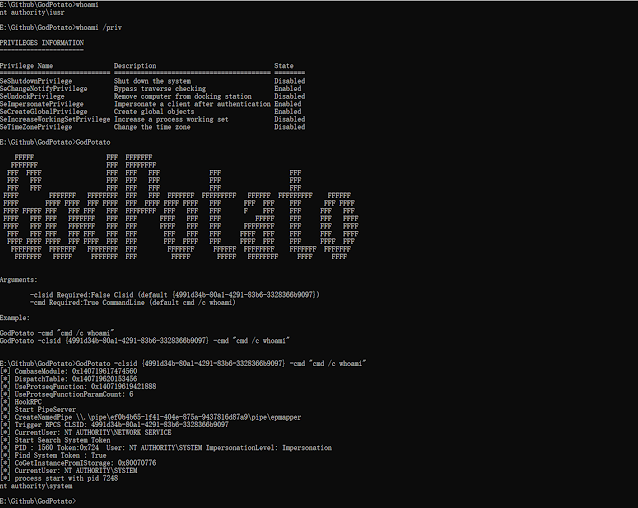
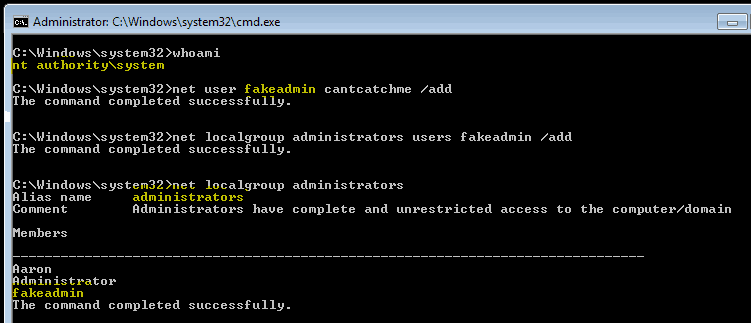
NoFilter: Tool that Escalates Privilege Abusing Windows Filtering Platform - GBHackers on Security | #1 Globally Trusted Cyber Security News Platform