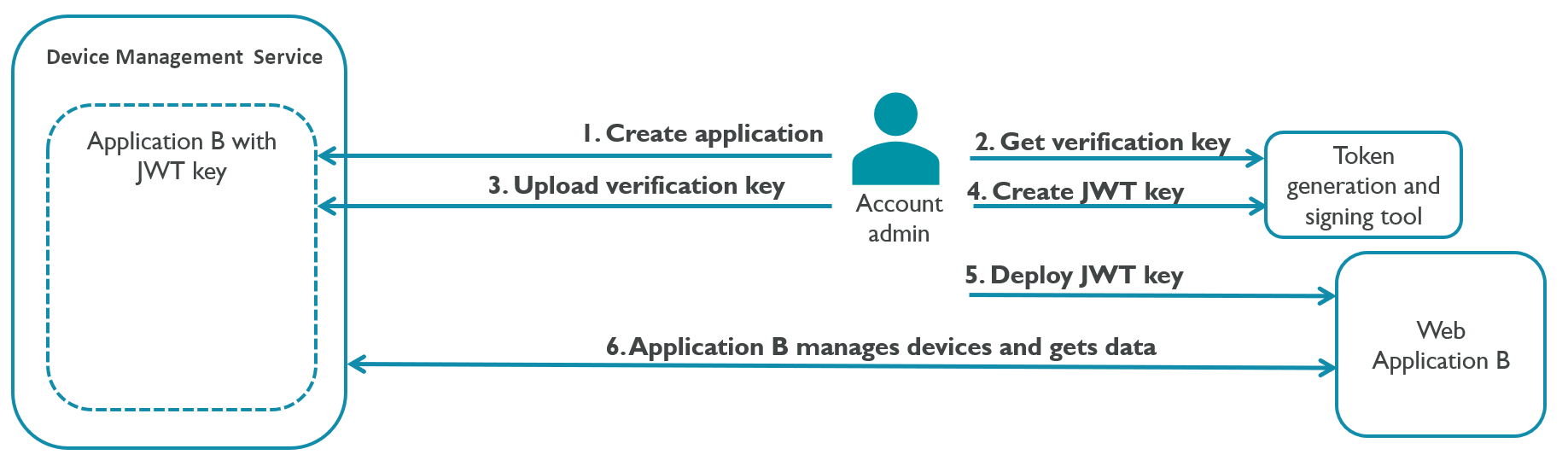
Secure your Endpoints with JWT Tools, JWK encryption and decryption , create PEM Files on the fly - Security Salamander - Plugins - Bubble Forum
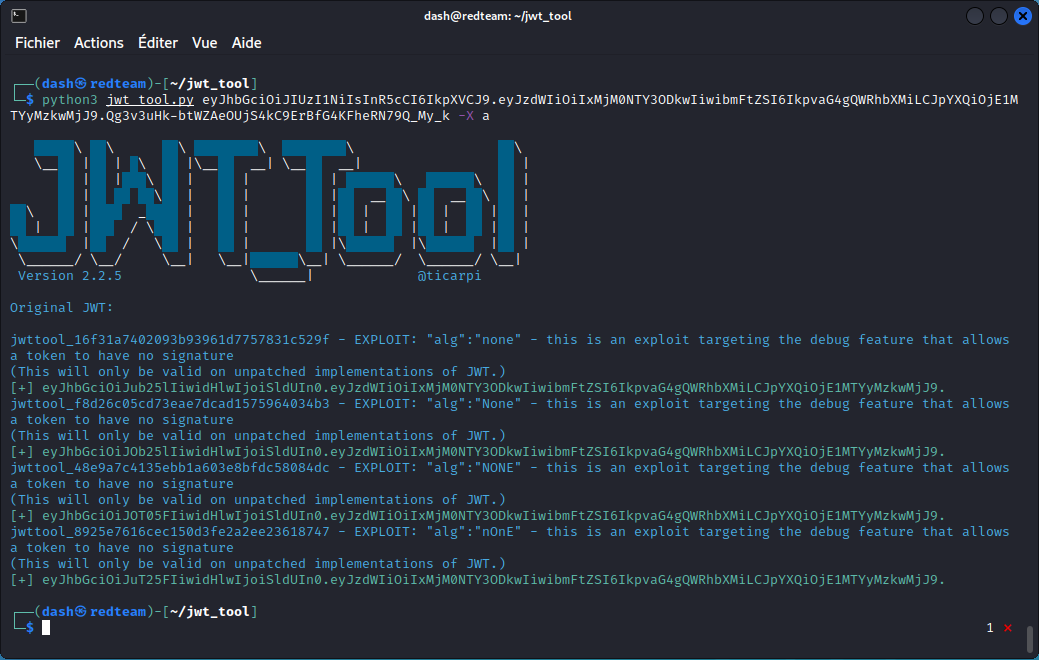
Hacking JWT Tokens: Bruteforcing Weak Signing Key (jwt_tool) | by Shivam Bathla | Pentester Academy Blog
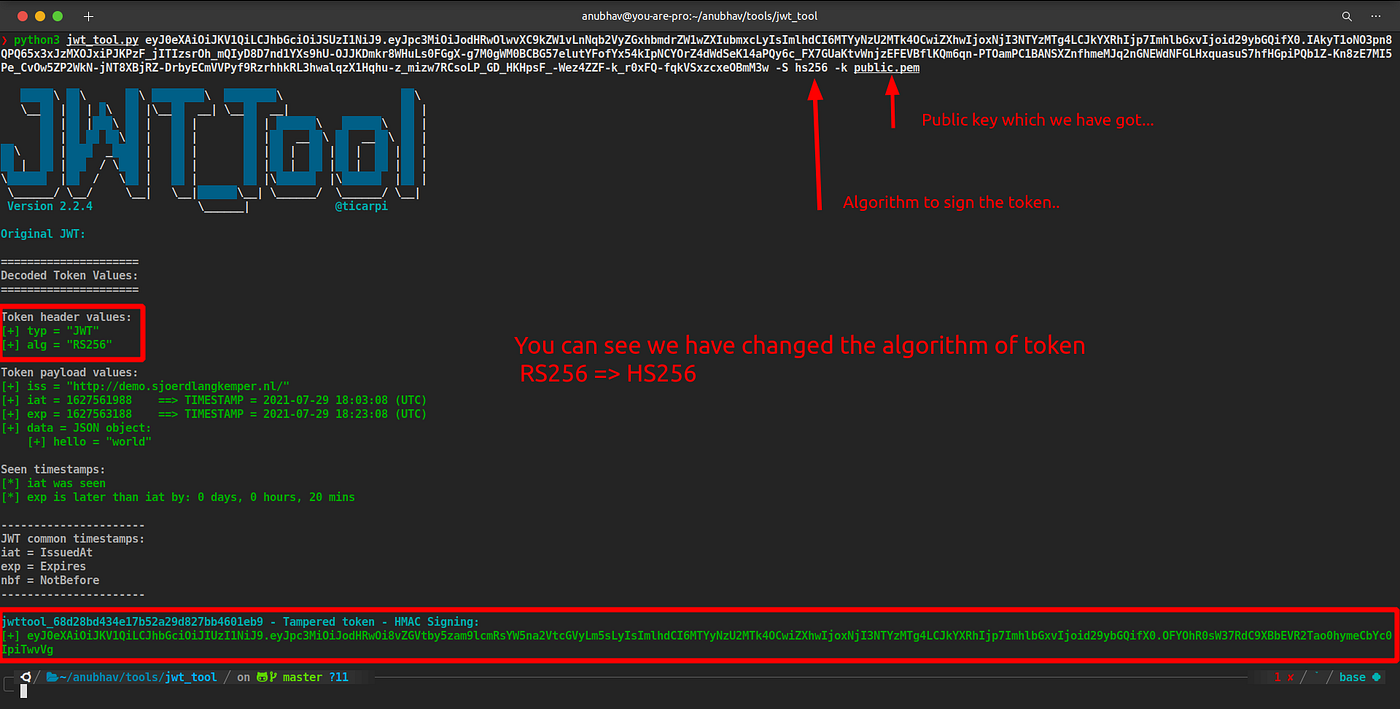
Attacks on JSON Web Token (JWT). In part1 of the article, I introduced… | by Anubhav Singh | InfoSec Write-ups
Hacking JWT Tokens: Bruteforcing Weak Signing Key (jwt_tool) | by Shivam Bathla | Pentester Academy Blog





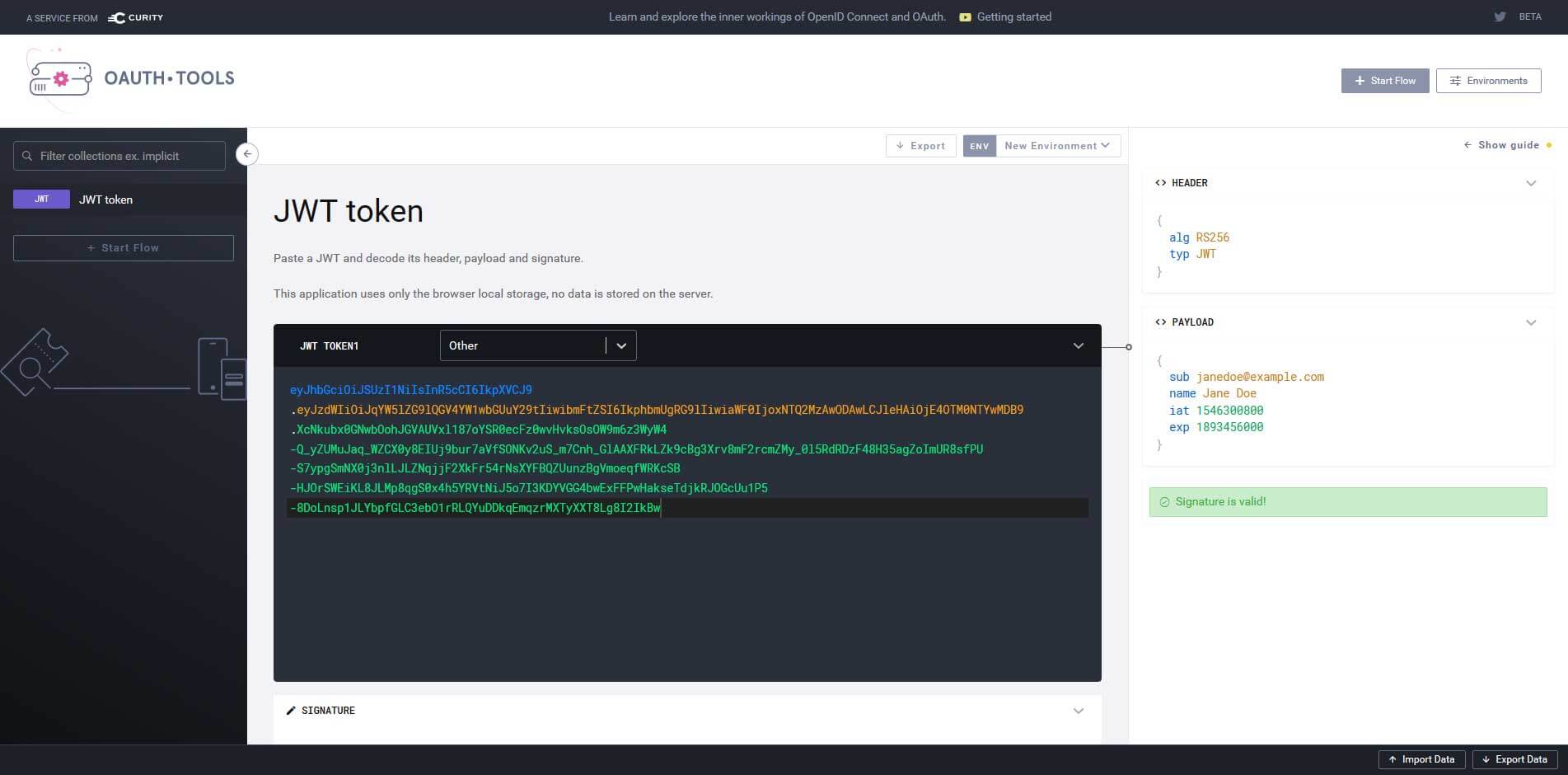
![Introducing JWT Tool ][ ticarpi Introducing JWT Tool ][ ticarpi](https://www.ticarpi.com/assets/images/jwt_tool.jpg)